Understanding Social Engineering Tactics: How Hackers Manipulate Human Behavior
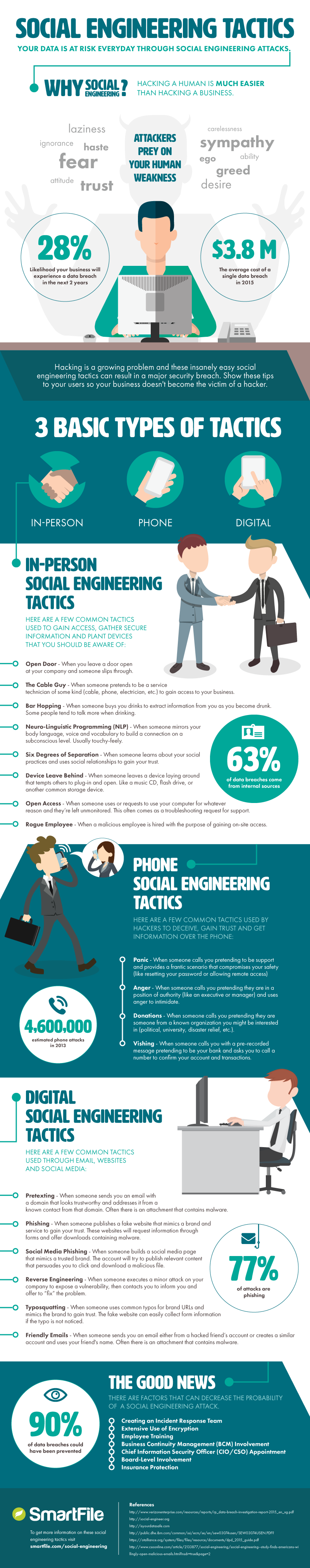
Social engineering attacks have become one of the most insidious threats in the world of cybersecurity. Unlike traditional cyberattacks that target systems and software, social engineering targets human behavior, exploiting human trust, ignorance, or psychological vulnerabilities to gain unauthorized access to data and systems. The infographic titled “Social Engineering Tactics” illustrates just how dangerous and effective these attacks can be, as well as how they prey on our natural tendencies like trust, sympathy, and fear.
Why Social Engineering?
Hackers often prefer social engineering because it can be far easier to “hack” a human than it is to penetrate a highly secure system. Organizations invest heavily in firewalls, encryption, and other defenses, but people remain the weakest link in cybersecurity. The data presented in the infographic underscores this, with 28% of data breaches involving insiders. This means attackers are often leveraging individuals within an organization—whether willingly or unknowingly—to gain access to sensitive information. Even more alarming, the average cost of a data breach can reach up to $3.8 million—a staggering figure that highlights the economic impact of these attacks.
3 Basic Types of Social Engineering Tactics
- In-Person Tactics:
Hackers use face-to-face interactions to manipulate individuals into revealing information or granting access. For instance, an attacker may impersonate an IT technician (the “Cable Guy” tactic) to gain physical access to a company’s network, or they may pose as an employee who has “forgotten their badge” to gain entry to a restricted area. In-person tactics take advantage of natural human tendencies toward politeness and trust. Shockingly, 63% of data breaches stem from internal sources, showing just how often these manipulations take place within organizations. - Phone-Based Tactics:
A widely known phone-based attack is vishing (voice phishing), where hackers call targets and pretend to be someone in authority to trick the person into revealing sensitive information. A common example is a hacker pretending to be from the bank or IT department, asking for credentials or passwords. Whaling targets high-ranking officials, such as CEOs, by crafting personal and believable scenarios, often involving financial or urgent issues. According to the infographic, 4.6 million phone-related fraud cases occur annually, demonstrating how effective this method remains. - Digital Tactics:
The digital landscape provides hackers with a plethora of social engineering opportunities, including phishing and pretexting. Phishing, which accounts for 77% of attacks, is the most common, where attackers send fraudulent emails that appear to be from reputable sources. These emails often contain malicious links or attachments. Meanwhile, pretexting involves crafting a fake scenario to gain the victim’s trust—attackers might pretend to be from tech support or a trusted vendor, seeking access to secure systems.
Common Social Engineering Techniques
- Phishing: The most well-known tactic, phishing involves sending fake emails designed to trick users into clicking malicious links or providing sensitive information. It remains the most prevalent form of attack, responsible for more than three-quarters of social engineering attacks.
- Pretexting: Hackers fabricate a believable scenario to gain access to sensitive information. This tactic relies heavily on the attacker’s ability to convince their victim of their legitimacy.
- Tailgating: This in-person tactic involves following an authorized individual into a restricted area without proper credentials, leveraging the politeness of people who hold doors open for others.
- Reverse Engineering: Some attackers will use acquired data to manipulate individuals into providing more valuable information or access, expanding the breach further.
How to Combat Social Engineering Attacks
The good news is that there are proven methods to reduce the risk of falling victim to social engineering attacks. The infographic emphasizes several key strategies:
- Employee Training: The human factor is the weakest link in cybersecurity. Regular training can help employees recognize phishing attempts and understand the importance of verifying requests for information.
- Encryption: Encrypting sensitive data ensures that even if it is accessed, it cannot be easily used by the attacker.
- Business Continuity Management (BCM): Having clear protocols in place for business continuity ensures that an organization can quickly respond to and recover from attacks.
- Incident Response Team: Having a dedicated team trained to respond quickly to social engineering attempts is crucial for minimizing damage and preventing breaches.
Conclusion
Social engineering exploits the vulnerabilities inherent in human psychology, making it a particularly dangerous form of attack. However, as shown in the infographic, the likelihood of these attacks can be significantly reduced through awareness, training, and strong organizational practices. With 90% of breaches being preventable through these measures, the responsibility lies with both individuals and organizations to build defenses that account for human weaknesses, ensuring they remain a step ahead of social engineers.